7540
Views & Citations6540
Likes & Shares
The hotel security environment provides unique situations of insecurity that provides thriving conditions for crime. These conditions include robberies, drugs, cyber- crimes, and injuries and deaths. Due to poverty and unemployment most youth are motivated to engage in criminal activities as a means of survival. This creates a unique crime environment as a soft target within the hotel and tourism industry due to high flow of human traffic (Mansfield, 2006).
However, the conditions that encourage crime differ from one star rating hotel to the other meaning that the crime profile is different in the regions. This provides a challenge as far as security prevention strategies are concerned because security standards vary significantly (Mansfield, 2006). In terms of hotels‟ security standards, effective and functional security devices are insufficient, and the overall effectiveness to respond to crime situations in most cases is wanting.
This study gives a pointer onto the effect of security on hotel performance. However, the results derived from the study only point out that there is a relationship between terrorism and hotel performance.
Therefore, the importance of this study is on its attempt to evaluate the effects of insecurity on the hotels’ performance. Specifically, this study sought to address one hypothesis:
H01: There is no significance difference between the security procedures and the security training in the hotel industry by star rating.
CONCEPTUAL FRAMEWORK
Figure 1 illustrates the research framework showing the relationship between the study variables.
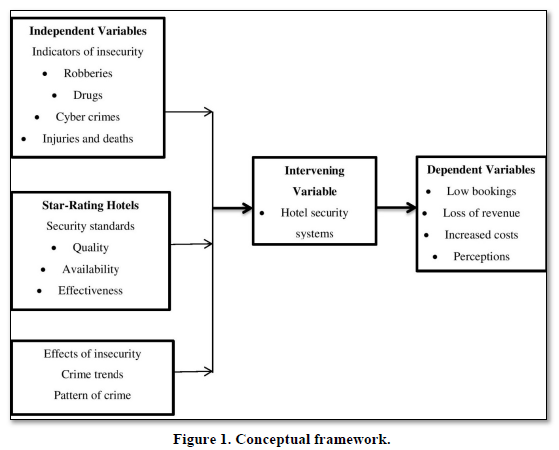
Mutai (2000; 104) points out that a conceptual framework is derived from theory, it identifies the concepts included in the complex phenomenon and will show their relationships. Conceptual framework was constructed to show the hypothesized variables related to hotel security 77 competitiveness. The conceptual framework for this study begins with the recognition of the hotel performance competitiveness environment. As mentioned earlier, the security environment is a unique environment with different security structures and policies in the hotel industry.
The hotel security environment provides unique situations of insecurity that provides thriving conditions for crime. These conditions include robberies, drugs, cybercrimes, and injuries and deaths. Due to poverty and unemployment most youth are motivated to engage in criminal activities as a means of survival. This creates a unique crime environment as a soft target within the hotel and tourism industry due to high flow of human traffic (Mansfield, 2006). However the conditions that encourage crime differ from one star rating hotel to the other meaning that the crime profile is different in the regions. This provides a challenge as far as security prevention strategies are concerned because security standards vary significantly (Mansfield, 2006). In terms of hotels‟ security standards, effective and functional security devices are insufficient, and the overall effectiveness to respond to crime situations in most cases is wanting. Therefore in a bid to come up with an effective security management strategy for the hotel and tourism industry, it is vital to analyze the security environment in the two geographical destinations (Gimonde, 2007).
A framework is required to analyze these security threats. First it is vital to analyze the nature and topology of crime across the different star rated hotels which provides an avenue to establish whether different star rated hotels require the same intervention efforts or not. Linked to this, is the assessment of vulnerabilities to insecurity in the 78 same location? Are there rated hotels in the two geographical locations where one would be more vulnerable than the other? Vulnerability to security affects other facets as well. First vulnerability to sensitizes to insecurity shapes the safety perception and attitude towards insecurity. It also affects general feeling of safety of the guests in the hotel and tourism industry. Finally understanding vulnerabilities provides one venue for tailoring home grown strategies to curb crime. Finally in addressing security issues, prevention strategies are important to consider. Prevention strategies are informed by inputs from crime typology and nature of crime in the underlying differences. These strategies also benefits from crime trends in the hotel and tourism industry Mansfield, 2006).
LITERATURE REVIEW
In a study on assessing the cost of insecurity in the hotel industry, Frey, Luechinger, and Stutze (2007) found that hotels have become a frequent target of terrorist activities in recent years. For this reason, hotels are being affected as individuals planning their holidays are less likely to choose a destination with a higher threat of terrorist attack (Punpugdee, 2012). Host countries providing hotel services which can be easily substituted, are, therefore, negatively affected by terrorist attack to a substantial extent (Konald, 2012).
This is because the affected hotels experience loss of avenue and incur increased costs due to beefing up security (Konald, 2012). The consequences of any terrorist acts and threats have economic, social, and psychological effects not only to the hotel industry stakeholders‟ but also the national economy of a destination (Konald, 2012).
In a report in Kenya by (Bado, 2012) observed that tourism industry in Lamu had dropped by more than 50% from January to July, 2011 due to insecurity and travel advisories issued by European countries. Most of the hotels have incurred huge losses as a result of cancelled bookings that have caused great harm to the industry even as the government struggles to improve the situation. The hotel industry within Lamu was forced to lay off between 10-15% of the hotel staff to cut off further loss arising from the insecurity.
Konstanze, 2009 in a survey of 25 global resort destinations observed that destinations were affected by the geopolitical tensions in some countries. For example, the war in Iraq and security concerns continued to influence travel patterns and consequently hotel performance. The World Tourism organization estimated that global international visitors‟ arrivals fell 1% in 2003 as travelers opted to stay closer to home and thus resorts within Europe, the Middle East and the Caribbean were beneficiaries of increased intra-region travel.
Unfortunately, tourists and travelers have always been victims of violent and non- violent crimes such as robbery, rape; assault and murder have negative effect on tourists than personal property crimes (Chon & Sparrow, 1995). Violent crimes are, at times, life altering and can be more devastating to a victim than non-violent crimes such as theft (Pizam, 1999). Incidents such as the killing of a disabled American tourist on the AchilleLauro cruise ship brought massive media attention.
The effect of crime on tourist arrivals is a major concern to tourist destinations. Most tourist destinations try to paint a beautiful picture of their areas in order to entice travelers to visit (Sallows, 1989). The government as well as the media frequently plagued by criminal activities against tourists in the United States issues travel warnings for certain countries, Kenya included, warning potential tourists of safety/security concerns, sometimes suggesting that America avoids travelling to certain areas altogether (Yoel & Pizam, 2006).
The news media also plays a role in the dissemination of this information (Yoel & Pizam, 2006). As an example, an annual personal safety survey by Mercer Human Resource Consulting, cited in the British Daily Telegraph, Starmer Smith, 2003 listed the world’s most crime prone tourist destinations: Cape Town, South Africa: Mexico City, Mexico; Washington DC, USA; Rome, Italy and Athens.
Negative media attention on a tourist destination in relationship to crime incidents can sometimes be blown out of proportion (Crystal, 1993). In the case of the murder of the pregnant German mother in Miami and a male British tourist near Tallhasses, Florida, tourism to Florida declined significantly (Yoel & Pizam, 2006). Media accounts suggested that crime was rampant against Florida tourists while official statistics told another story (Yoel & Pizam, 2006).
According to Benson, 2011 in a report on how improvements in guest identification technology are helping to fight terrorism and cyber-crime, it was indicated that although this is a great innovation, identifying hotel guests in the first place is no longer a simple procedure. Now the hospitality industry is faced with cyber-crime and credit card fraud as hackers target hotels and resorts in increasing numbers with more organized and sophisticated means of doing so. There could be relatively unprotected sources of thousands or even millions of credit card accounts and personal details that cyber criminals can try to access. One security expert warned that rather than searching through many industries for vulnerable targets, hackers are increasingly targeting specific sectors whose systems they believe are susceptible and lucrative. There have been cases where cyber criminals have been able to siphon credit card information from hotel databases without being detected for months.
RESEARCH METHODOLOGY
Target population
The target population for this study comprised all Hotel Managers, Hotel Security Managers, and Division Room Managers in 3-5 hotels in Mombasa and Nairobi, which are approved by hotels and Restaurant Authority within the Ministry of East African Affairs, Commerce and Tourism, the (Kenya Gazette, 2003. These cadres of respondents have critical, useful and confidential security information in the hotel industry as they make decisions concerning security issues. A list of all the hotels rated from three, four to five was compiled and this formed the sampling frame.
In this case, the criterion was the star rating. Star rated hotels are luxurious hotels with exceptional modern and technical amenities and offer the highest standards of accommodation, service and comfort. Tourists frequent these hotels because they are believed to offer high standards security (GoK, 2007).
Sampling procedure and data collection
Nairobi and Coastal regions were purposely selected as study sites because they possess a pride no other towns in Kenya does and the main activity is tourism particularly the coastal area. Nairobi hosts business and transit travelers. Stratified Random Sampling (SRS) was used to select the key respondents in 3-5 star hotels. These included; Hotel Managers, Hotel Security Managers, Front Office Managers, Accountant and Division Room Managers. Other stakeholders included Kenya Tourism Board; Kenya Police Tourist Unit, Kenya Hotel Keepers Association, Provincial Security Committee, Ministry of Tourism and Information, Kenyan Navy. One key respondent in each stratum in both regions was selected. The main stratum was the major job categories in the hotels. Further, the stratification of a proportionate allocation to size was extended to adjust the number of respondents for stratum. Security managers, Hotel managers, Front Office Managers and Division Managers because of their few numbers were purposively selected to allow each sub-group to be adequately represented (Table 1).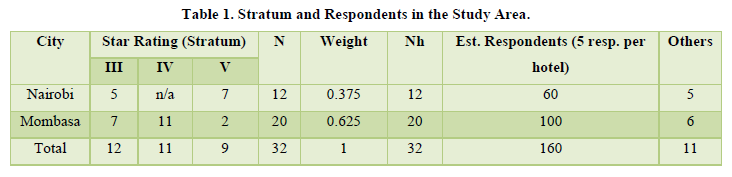
The Security Managers provided information on crimes histories, if any, in the establishment. They also provided information on whether there are any variances on security crimes committed and the corrective actions taken. The Hotel Manager provided information on security strategies applicable in their establishments. The recruitment of security personnel’s qualifications required and the forms of security available. Division Rooms Manager provided information on those acts employees might be doing to defraud the guests and their employers. Their level of training provided an insight in their competence or lack of it in understanding and interpreting security procedures and policy.
Other stakeholders provided information on security policies in place, mechanisms to tackle crimes particularly those affecting the hotel industry. The collaborations between these stakeholders and the hotel industry, the challenges they encounter and pro-active strategies in place to curb cases of insecurity in both regions.
The stratified study requires that a researcher establishes insecurity information on the criteria or attributes that units of study must possess. The purpose of selecting the case or cases is to develop a deeper understanding of the phenomenon under study (Kothari, 2007).
Data Collection Instruments
The study used methodological triangulation approach to collect the required data using self-completion questionnaires, interview schedules and observation checklists. This approach offered the prospect of improved confidence in the collected data (Kothari, 2007).
Questionnaires
Both structured and semi-structured questionnaires were administered to Division Rooms Manager to collect data on crimes committed in the rooms by guests. The researcher decides the sequence and even the wording of questions because they have the advantage of collecting information from many respondents within a short time.
The respondents are free to offer information because: they are assured of their anonymity. According to Mugenda and Mugenda, 2003 respondents equally control the data collection process in that they can fill in the questionnaires at their convenience, answer in any order or give unique responses.
Interview Schedules
The interview guides were semi-structured and administered to Security Manager, Hotel Manager, and Room Divisions Manager. When using interview guide, the researcher decided the sequence and even the wording of the questions. Notes were taken during these sessions. The interview was recorded in individual schedules. These were later transcribed in order to verify the notes and also fill the gaps. According to Mugenda & Mugenda, 2003 skilled interviews, through probing can clarify vague statements to obtain in-depth, personal and sensitive information.
Observation Checklist
Observation checklist, (Appendix IX), was used to capture non-verbal occurrences. The researcher recorded the security practices and movements of security guards in the hotel industry as well as the movements of guests within the hotel premises. The types of security facilities used and design of the premises in regard to security was noted.
Secondary Data
Documents such as daily occurrence incidents and annual reports on security issues were used to complement other sources of data (Table 2).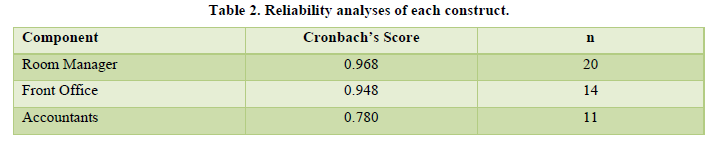
In assessing the reliability of the research instrument, Cronbach’s alpha test (1951), which is a common model used to measure reliability and validity of a research instrument, was used. The reliability analysis results are exhibited in Table 2. The table reveals that alpha coefficients for room manager, front office and accountant’s responses were 0.968, 0.948 and 0.780 respectively. From the findings it can be concluded that the constructs measured had the adequate reliability for the subsequent stages of analysis since all the Cronbach values were greater than 0.67 (Aiken, 1999).
Data analysis
The questionnaires were coded for easy data entry. After cross checking the questionnaires for any missing entries, a data base was designed in MS Access which allowed the researcher to set controls and validation of the variables. The entered data was cleaned before the onset of actual data analysis. Exploratory Data Analysis (EDA) was utilized in the evaluation of the outliers and any missing data points were addressed. Descriptive statistical data analysis methods were used at the initial stage and the findings presented in summary tables and graphs where applicable. Inferential statistics were used to analyze the data and to test the hypotheses.
On establishing the distribution functions (normal/non-normal) for the variable an independent sample t-test for the continuous variable in the hotel industry were undertaken while for variable with non-normal distribution were used.
Factor analysis using Principal Component Analysis (PCA) with varimax rotation was used to assess the relative significance of various factors relatable to security and safety issues in the hotels. Kaiser-Meyer-Olkin (KMO) test and Bartlett’s test of sphericity were both used to measure the sampling adequacy and to test the level of significance. P-value less than 0.05 were considered appropriate for factor analysis. For factor analysis with PCA, all variables are required to have communalities greater than 0.5. Therefore, all items in the scales with communality less than 0.5 were excluded from the overall factor analysis.
Odds Ratios (OR) and associated 95% confidence interval (CI) was calculated to identify the factors that are more likely to explain the explanatory variable. P-value of less than 5% (P<0.05) was considered statistically significant. Qualitative data analysis was used in the study. Qualitative methods sought to develop a systematic analysis of qualitative responses from Questionnaire. Qualitative data was organized according to themes. This facilitated the interpretation of information necessary in answering the research problem.
RESULTS
Sample
Response Rate Respondents
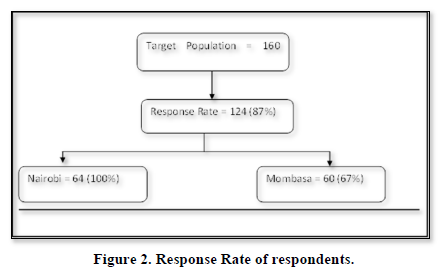
Out of one hundred and sixty (160) questionnaires distributed, one twenty four (124) were filled and received back. This makes a response rate of 87% as indicated in Figure 2. This response rate was way above the 60% that is generally used as a threshold.
Distribution of Age profile of Respondents in Hotels
The respondents were asked to indicate their age brackets. The findings are indicated in Table 3.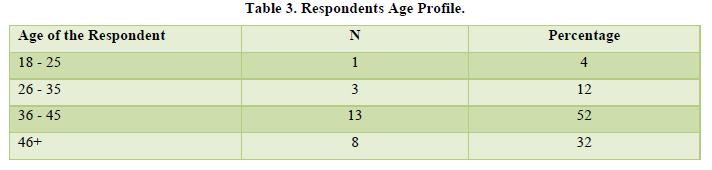
Age is an important demographic variable and is the primary basis of demographic classification. The findings from this study indicated that employee population is predominantly youthful 72% being below 45 years of age. Other studies have also shown similar age distribution in Nairobi city APHRC (2002) had over 75% were found to be within this age bracket. The potentiality of the hotel employees is attributed to that majority of the workforce within the labor production employee age and engages actively in employment. However, 32 % of the respondents in this research were above the age of 46 and above. The implication of this finding is that, the study targeted high managerial positions which also require experience and hence the age between 36- 46 years is in tandem with longevity in workplace.
Distribution of Educational Qualification of Respondents in Hotels
The study sought to establish the level of education of the respondents. The findings are indicated in Table 4. Eighty percent (80%) of the respondents have attained a university degree and above. Only 20% did not have a degree. Therefore, the hotel employee population in terms of their educational attainment can be described as higher (Table 4).
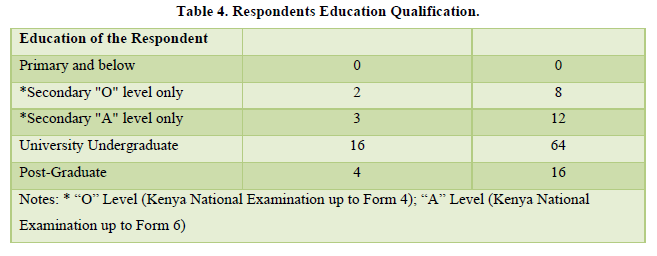
Education is a key determinant of the lifestyle and status an employee enjoys in the workplace. Other studies by KDHS (2008-09 have consistently shown that educational qualification has an effect on the perception and attitudes of the respondents.
The distribution of educational qualification of respondents star rating hotels indicated a more male dominated employee with degree and above working in 4 to 5 star hotels. The implications of this is that a more educated workforce is more adaptive to dynamic security intervention measures required than a less educated workers (Nzioka, 2013).
The security parameters are evolving and challenging to the hotel operators. This therefore requires informed minds on security procedures and standards to mitigate any security lapse in the hotel industry.
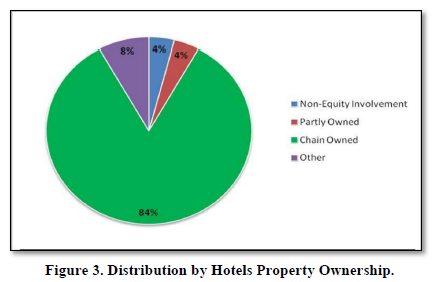
Distribution of Hotels by Property Ownership
From the Figure 3 on property ownership, 84% indicates a strong skew towards chain ownership of the hotel property. Other hotels (4%) were individually owned. This result is consistent with Ikiara et al, (2001) report that Kenya Tourist Development Corporation (KTDC) Act (CAP 382) provides the regulatory framework for the development of the Private sector’s tourism enterprises. Since independence, the government has been a major participant in the ownership and management of tourism enterprises through the KTDC. This enabled it to control a sizeable share of the tourist market and to expand tourism infrastructure. However, competition from the private sector was encouraged. In fact, the KTDC was mandated to offer soft loans to small hotels owned by Kenyans and to provide long-term loans to private sector hotel investors. Investment incentives, such as generous duty remissions on imported inputs, were extended to foreign investors.
Accountants Concern for Security Issues
The factor analysis of the hotel accountants to establish their level of concern concerning the safety and security issues was conducted. Kaiser-Meyer-Olkin (KMO) and Bartlett’s test of sphericity addressed the sample adequacy and the level of significance (KMO measure of sample adequacy = 0.653; Bartlett’s Test: χ2 =168.580, P < 0.001). Based on these findings, factor analysis was fitting. Results in Table 5 indicate that only two components were extracted at an eigenvalue equal to or greater than 1 and accounted for 71.937 per cent of the total variance in the level of concern pertaining hotel accountants‟ security and safety issues.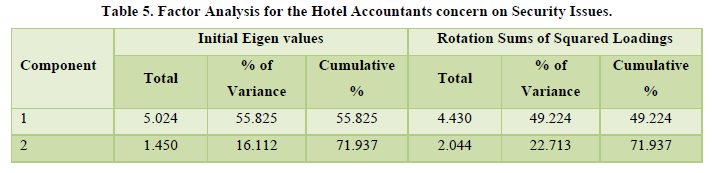
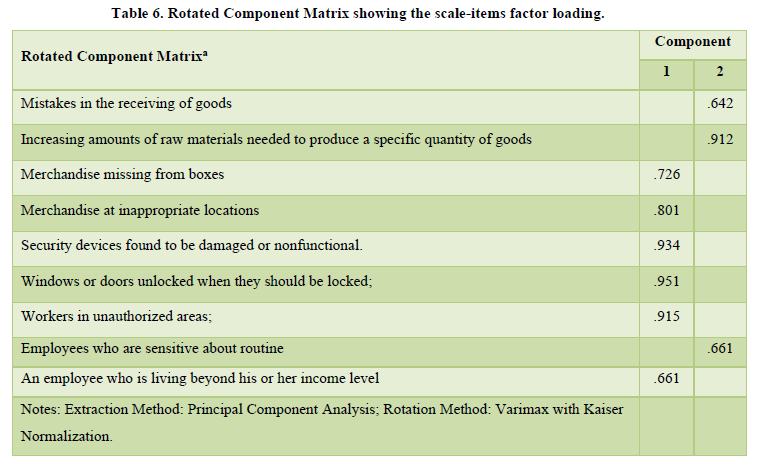
Based on the results in Table 5, the first extracted component accounted for 49.224 per cent of the total explained variance in the accountants concern regarding the safety and security issues. This component included merchandise missing from boxes, merchandise at inappropriate locations, security devices found to be damaged or nonfunctional, windows or doors unlocked when they should be locked and workers in unauthorized areas. The implications of this finding are that hotel management has a great concern in security measures applied in the hotel industry. These are internal control aspects within the kitchen and the store operations, which affects hotel’s profitability.
The second component accounted for 22.713 per cent of the total explained variance and comprised of mistakes in the receiving of goods, increasing amounts of raw materials needed to produce a specific quantity of goods, and employees who are sensitive about routine. These are internal vulnerabilities which the hotel management needs to address by putting in stringent measures to increase profit margins in the food and beverage operations. The analysis of the rotated component matrix is shown in Table 6.
Evaluation of the Effects of Insecurity on the Hotels’ Performance
The third objective was to evaluate the effects of insecurity on the hotel’s performance in the hotel industry in Nairobi and Mombasa region. Additionally, in this section, the following hypothesis is tested. The Managers’ perception on the distribution of cost of security in hotels by Region and star rating hotels is presented in Table 7.
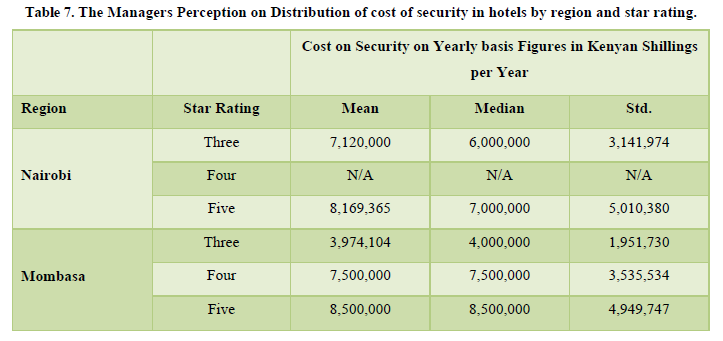
The data in Table 7 shows the cost of security in the studied regions. In Nairobi the mean average cost of security in a 3 star hotel is Kshs. 7,120,000 million per year. Whereas in a five star hotel its Kshs. 8,169,365.00 million. In Mombasa region, the mean average cost of security is Kshs. 3,974,104 million in a 3 star hotel whereas its Kshs. 8,500,000 million in a five star hotel annually. The mean cost of security in a three star hotel is Kshs. 3,974,104, which is a significant difference of Kshs.3, 145,896 million between a three star hotels between Nairobi and Mombasa. Therefore hotels in a 3 star category in Nairobi spend more by 56 percent than the Coastal hotels in the same category.
Hotels are increasingly seen as soft targets by terrorists for being open and accessible but the industry is determined to deal with the terrorist threats in a way that is sensitive to the needs of its guests, Parton (2007). Hotel managers know that biometric technology clearly has a role to play in their operations and future developments like biometrics will bring benefits. But at the same time, to retain their appeal, hotels need to safeguard guest comfort and convenience that make them desirable places to stay.
Hotels are expected to use biometrics to improve room security, improve customer convenience, control access to restricted areas, and limit access to customer data, (Jones &Rustenburg, 2006). Also, the reliability of biometric systems is an issue with hoteliers and according to one very recent study cost still seems to be one of the major barriers to adoption of biometric technology applications (Cobanoglu, 2010).
Most studies done on biometrics involve the industry, authentication and security (Willis, 2008). It has been shown that negligence of innovation technologies produces consequences that foster bad impressions from guests. Strong evidence suggests that innovation technologies and its negligence engage in a reciprocal relationship that has a short and long-term effect on the guest’s future opinion regarding the service quality of hotel establishments, (Cobanoglu, 2010).
The market for biometrics in the hotel industry especially in the Kenyan hotels was in the infant stages with only a few of hotels adopting biometric technology so far. Continued security concerns, declining hardware and network technology prices, and guest comfort with the technology will lead to advances in market adoption (Jones & Rustenburg, 2006) (Figure 4).
Managers Perception on Distribution of Expenditure Cost on Security in Hotels by Region
Figure 4 shows data of the cost of expenditure on security in the two regions. From the said data, Nairobi spends huge investments on security matters as compared to the Coastal region. Nairobi city hosts many international embassies and also is the headquarters of United Nations Environmental Programs. The majority of both international and domestic tourists seek their accommodation in at least these star rating hotels. The Mombasa region has not invested much in security devices, however, there were two hotels which were outliers; hotel numbers 7 and 14. The reason for this variation is that these are chain hotels with similar security standards whose headquarters’ is based in Nairobi.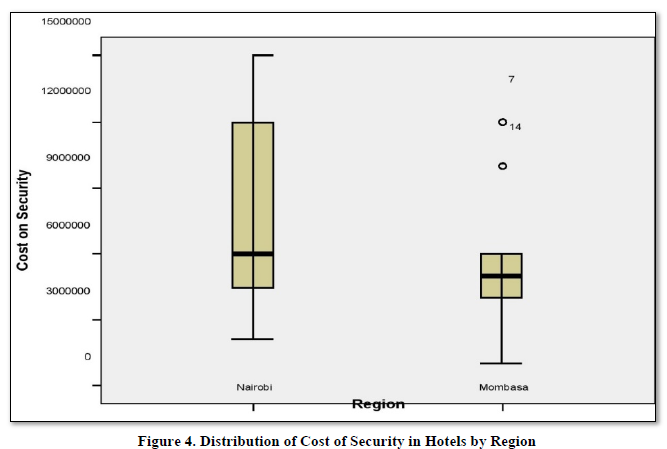
As noted from Figure 5 the higher the star rating hotel, the more the cost of security invested in the hotels regardless of the region. The five star hotels had heavily invested in security in terms of surveillance devices, hiring of extra private security personnel as well as security personnel disguised as staff. Equally the same are 4-star hotels who have also upgraded their security status to measure up with the challenges of insecurity and crimes. However, there was a hotel number 15 under the three star hotels which has invested highly in security arrangements.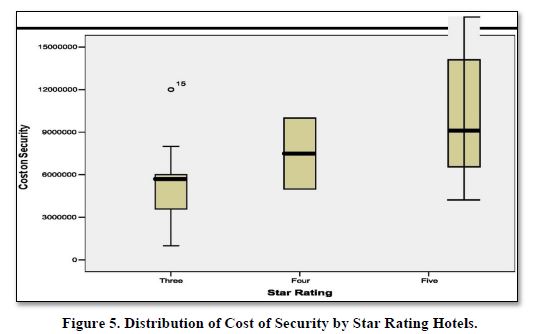
Nevertheless, within the lower hotel ratings stars (3 and 4) there was a notable variation within the amount spent on the security with 3 stars having the highest variation. Many hotel managers agree that some hotels have been unwilling to risk alienating their clients by incorporating more cumbersome security measures such as identity and key checks upon entry, baggage screening, and more extensive standoff areas. Guests might consider those measures inconveniencing and thus they could directly and negatively affect business. Moreover from a business perspective, it can be difficult to justify the investment of millions of dollars in security precautions when the returns cannot be quantified. Given the highly competitive nature of the industry and guests reluctance to accept inconvenient security practices hotel owners often have been forced to take the calculated risk that their businesses will not be targeted.
Hotel security has traditionally focused on safety of guests and their property, fire prevention and natural disaster contingencies. Due to escalating cases of terrorism, many hotel managers interviewed stated that they are grappling with new concerns of the travelers globally. Majority of the managers interviewed concurred that the increase of security costs in the hotel industry has led hotels to increase their rates to recover from cost of security investment. This view is consistent with another study by Power& Barrowe, 2006 which showed that some business travelers were willing to pay $7.73 more on average in a room rate for a more secure lodging property $ 10.75 extra per day for tighter security combined. The rate premium was $9.97 for all respondents.
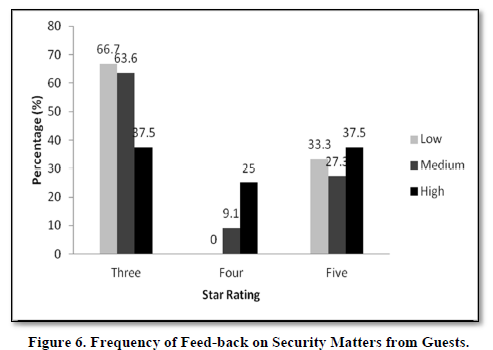
The Managers’ Perception on Frequency of Feed-back on Security Matters from Guests
Figure 6 indicates the frequency of feedback on security matters from guests. About 66.7 percent of the three star hotels indicated that they get guest feedback while 50 percent bi-annually and 33.3 percent perform training on monthly and quarterly basis respectively. In the four star category of hotels, 50 percent indicated that they undertake training on weekly basis. 33.3 percent and 16.7 percent indicated that they do their training fortnightly and monthly respectively. This finding indicates a worrying pattern in security training which appears to be of less concern in particularly five star hotels. However, these hotels showed high level of contention on security matters in both Nairobi and Coastal region. In the 3 star category, 66.7 percent of hotels stated that they undertake their training on quarterly and yearly basis respectively. On the other hand, 50 percent of the hotels do training on weekly, monthly and a yearly basis respectively.
H1 A direct positive relationship exists between investment in security management systems and high guest turnover in the hotel industry.
A Pearson correlation between investment in security management systems and guest turnover in the hotel industry is presented in Table 8. The investment in security aspects were not replicated into the hotel increase in occupancy. The might be a short cyclic event which might need time to observe the results of investment. Maybe this is a long term effect.
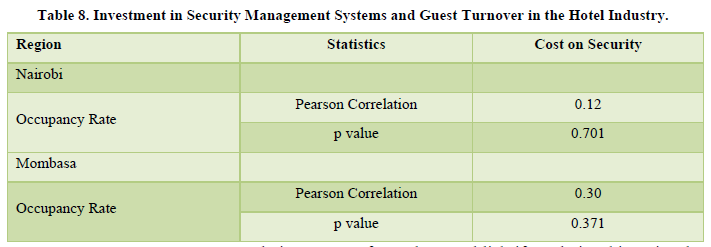
A Pearson Correlation was performed to establish if a relationship existed between investment in security management and guest turn-over ((P-value; 0.701, 0.371) in Nairobi and Mombasa respectively. Both regions had appositive correlation between occupancy and security investment. The hypothesis is therefore accepted. This indicates that as the hotel invested more, the higher the occupancy rate. However, this was not statistically significant. It portrayed a weak correlation (P-value >005). A Pearson correlation by star rating between investment in security management systems and guest turnover in the hotel industry is presented in Table 9.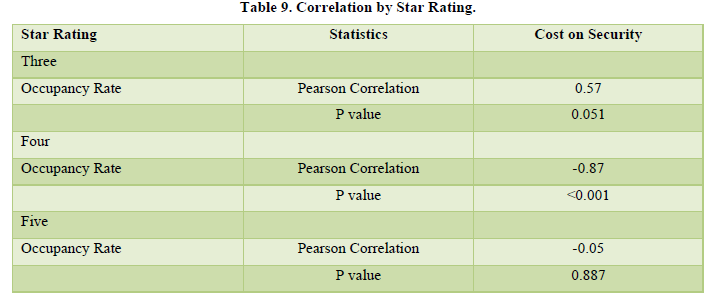
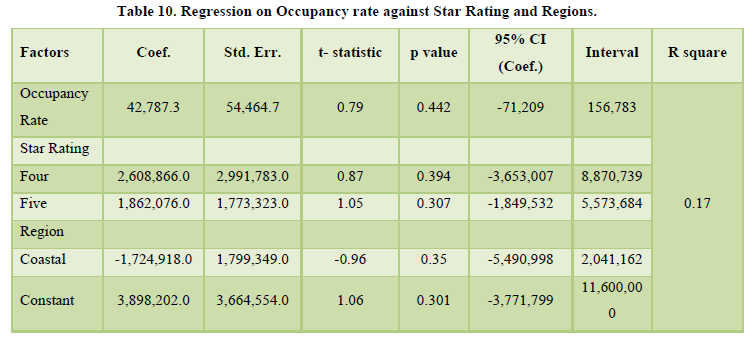
The positive correlation established in the Table 10 to portrayed an inverse correlation in some of the stars. For instance, higher stars (4 & 5) had a negative relationship of -0.87 and 0.05 respectively. For the correlation was evenly significant (p-value of > 0.05). The higher the occupancy rate the lower the investment of security in the hotel industry. The regression on occupancy rate against star rating and regions is presented in Table 10.
Distribution of Security Threats in Hotels by Star Rating
The Managers’ perception on distribution of security threats in hotels by star rating is presented in Figure 7.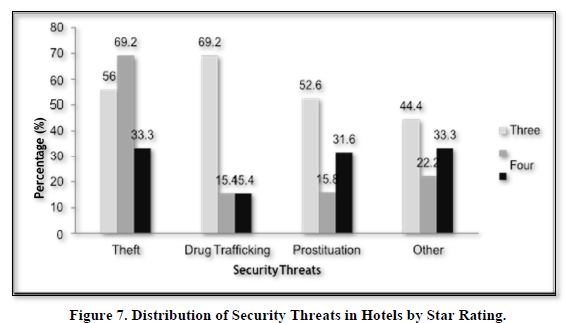
Figure 7 shows that 69.2 percent of 3 star hotels are involved in drug trafficking, closely followed by theft with 56 percent and 52.6 percent on prostitution respectively. In the five star hotels 32 percent and 31.6 percent had theft and prostitution respectively. On the other hand, 15.8 percent and 15.4 had prostitution and drug trafficking respectively. However, there were 12 percent cases of theft in four star hotels. It is important to note that all the four star hotels were found at the coastal region according to the Kenya Gazette of 2003 Hotels and Restaurant classification.
Distribution of Security threats in hotels by region
The managers’ perception of security threats in hotels by region is presented in Figure 8.
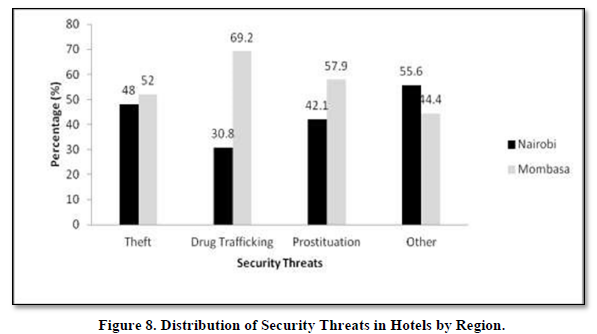
Figure 8 shows security vulnerabilities in the two regions. The Mombasa region had more cases of security threats than Nairobi. The hotels in Nairobi have invested more resources in security devices and training as it’s the regional hub not only in East Africa but also in Africa as a whole. In Mombasa, 69.2 percent had drug trafficking, while 57.9 percent and 52 percent had prostitution and theft respectively. The coastline is extensive and unmonitored which makes the region to be vulnerable. In Nairobi, 48 percent and 42.1 percent had theft and prostitution respectively. However, 30.8 percent had cases of drug trafficking.
DISCUSSIONS
One hypothesis was tested with regard to investment in security management systems and high guest. The hypothesis (H1): a direct positive relationship exists between investment in security management systems and high guest turnover in the hotel industry. A Pearson Correlation was performed to establish if a relationship existed between investment in security management and guest turn-over ((P-value; 0.701, 0.371) in Nairobi and Mombasa respectively. Both regions had appositive correlation between occupancy and security investment. The hypothesis is therefore accepted.
The findings from this study indicated that employee population is predominantly youthful 72% being below 45 years of age. Other studies have also shown similar age distribution in Nairobi city APHRC (2002) had over 75% were found to be within this age bracket. The potentiality of the hotel employees is attributed to that majority of the workforce within the labor production employee age and engages actively in employment. However, 32 % of the respondents in this research were above the age of 46 and above. The implication of this finding is that, the study targeted high managerial positions which also require experience and hence the age between 36- 46 years is in tandem with longevity in workplace.
The distribution of educational qualification of respondents star rating hotels indicated a more male dominated employee with degree and above working in 4 to 5 star hotels.
The findings on distribution of educational qualification of respondents in Hotels are indicated in Table 4. Eighty percent (80%) of the respondents have attained a university degree and above. Only 20% did not have a degree. Education is a key determinant of the lifestyle and status an employee enjoys in the workplace. Other studies by KDHS (2008-09 have consistently shown that educational qualification has an effect on the perception and attitudes of the respondents.
Based on the results in Table 8, the first extracted component accounted for 49.224 per cent of the total explained variance in the accountants’ concern regarding the safety and security issues. This component included merchandise missing from boxes, merchandise at inappropriate locations, security devices found to be damaged or nonfunctional, windows or doors unlocked when they should be locked and workers in unauthorized areas.
The second component accounted for 22.713 per cent of the total explained variance and comprised of mistakes in the receiving of goods, increasing amounts of raw materials needed to produce a specific quantity of goods, and employees who are sensitive about routine. These are internal vulnerabilities which the hotel management needs to address by putting in stringent measures to increase profit margins in the food and beverage operations. The analysis of the rotated component matrix is shown in Table 9.
The data in Table 10 shows the cost of security in the studied regions. In Nairobi the mean average cost of security in a 3 star hotel is Kshs. 7,120,000 million per year. Whereas in a five star hotel its Kshs. 8,169,365.00 million. In Mombasa region, the mean average cost of security is Kshs. 3,974,104 million in a 3 star hotel whereas it‟s Kshs. 8,500,000 million in a five star hotel annually. The mean cost of security in a three star hotel is Kshs. 3,974,104, which is a significant difference of Kshs.3, 145,896 million between a three star hotels between Nairobi and Mombasa.
Hotels are increasingly seen as soft targets by terrorists for being open and accessible but the industry is determined to deal with the terrorist threats in a way that is sensitive to the needs of its guests. Hotels are expected to use biometrics to improve room security, improve customer convenience, control access to restricted areas, and limit access to customer data, Jones and Rustenburg, (2006). Also, the reliability of biometric systems is an issue with hoteliers and according to one very recent study cost still seems to be one of the major barriers to adoption of biometric technology applications (Cobanoglu, 2010).
The market for biometrics in the hotel industry especially in the Kenyan hotels was in the infant stages with only a few of hotels adopting biometric technology so far. Continued security concerns, declining hardware and network technology prices, and guest comfort with the technology will lead to advances in market adoption (Jones & Rustenburg, 2006).
Figure 4 shows data of the cost of expenditure on security in the two regions. From the said data, Nairobi spends huge investments on security matters as compared to the Coastal region. Nairobi city hosts many international embassies and also is the headquarters of United Nations Environmental Programs. The Mombasa region has not invested much in security devices, however, there were two hotels which were outliers; hotel numbers 7 and 14. The reason for this variation is that these are chain hotels with similar security standards whose headquarters‟ is based in Nairobi.
As noted from Figure 5 the higher the star rating hotel, the more the cost of security invested in the hotels regardless of the region. The five star hotels had heavily invested in security in terms of surveillance devices, hiring of extra private security personnel as well as security personnel disguised as staff. Equally the same are 4-star hotels who have also upgraded their security status to measure up with the challenges of insecurity and crimes. However, there was a hotel number 15 under the three star hotels which has invested highly in security arrangements.
Hotel security has traditionally focused on safety of guests and their property, fire prevention and natural disaster contingencies. Due to escalating cases of terrorism, many hotel managers interviewed stated that they are grappling with new concerns of the travelers globally. Majority of the managers interviewed concurred that the increase of security costs in the hotel industry has led hotels to increase their rates to recover from cost of security investment. This view is consistent with another study by (Power Barrowe, 2006). which showed that some business travelers were willing to pay $7.73 more on average in a room rate for a more secure lodging property $ 10.75 extra per day for tighter security combined. The rate premium was $9.97 for all respondents.
Figure 6 indicates the frequency of feedback on security matters from guests. About 66.7 percent of the three star hotels indicated that they get guest feedback while 50 percent bi-annually and 33.3 percent perform training on monthly and quarterly basis respectively. In the four star category of hotels, 50 percent indicated that they undertake training on weekly basis. 33.3 percent and 16.7 percent indicated that they do their training fortnightly and monthly respectively.
A Pearson Correlation was performed to establish if a relationship existed between investment in security management and guest turn-over ((P-value; 0.701, 0.371) in Nairobi and Mombasa respectively. Both regions had appositive correlation between occupancy and security investment. The hypothesis is therefore accepted. This indicates that as the hotel invested more, the higher the occupancy rate. However, this was not statistically significant. It portrayed a weak correlation (P-value >005).A Pearson correlation by star rating between investment in security management systems and guest turnover in the hotel industry is presented in Table 9.
On the Distribution of Security Threats in Hotels by Star Rating, Figure 7 shows that 69.2 percent of 3 star hotels are involved in drug trafficking, closely followed by theft with 56 percent and 52.6 percent on prostitution respectively. In the five star hotels 32 percent and 31.6 percent had theft and prostitution respectively. On the other hand, 15.8 percent and 15.4 had prostitution and drug trafficking respectively. However, there were 12 percent cases of theft in four star hotels.
CONCLUSIONS
Based on the outlined study findings, several conclusions are drawn first the majority of the workforce has high academic qualification which is critical for understanding the security evolvement and trends in the hotel industry. The youthful mind is adaptive to the ever dynamic environment in regards to security perception and attitudes from both employees and guests.
Hotel managers know that biometric technology clearly has a role to play in their operations and future developments like biometrics will bring benefits. But at the same time, to retain their appeal, hotels need to safeguard guest comfort and convenience that make them desirable places to stay.
The Mombasa region had more cases of security threats than Nairobi. The hotels in Nairobi have invested more resources in security devices and training as it’s the regional hub not only in East Africa but also in Africa as a whole. In Mombasa, 69.2 percent had drug trafficking, while 57.9 percent and 52 percent had prostitution and theft respectively. The coastline is extensive and unmonitored which makes the region to be vulnerable. In Nairobi, 48 percent and 42.1 percent had theft and prostitution respectively. However, 30.8 percent had cases of drug trafficking.
Drug trafficking and prostitution are core vices which are rampant especially at the coastal region of Mombasa despite the government regulatory control measures which appears to be weak.
The positive correlation established in the Table 9 to portrayed an inverse correlation in some of the stars. For instance, higher stars (4 & 5) had a negative relationship of -0.87 and 0.05 respectively. For the correlation was evenly significant (p-value of > 0.05). The higher the occupancy rate the lower the investment of security in the hotel industry. The regression on occupancy rate against star rating and regions is presented in Table 10.
Many hotel managers agree that some hotels have been unwilling to risk alienating their clients by incorporating more cumbersome security measures such as identity and key checks upon entry, baggage screening, and more extensive standoff areas. Guests might consider those measures inconveniencing and thus they could directly and negatively affect business. Moreover from a business perspective, it can be difficult to justify the investment of millions of dollars in security precautions when the returns cannot be quantified.
There is a worrying pattern in security training which appears to be of less concern in particularly five star hotels. However, these hotels showed high level of contention on security matters in both Nairobi and Coastal region. In the 3 star category, 66.7 percent of hotels stated that they undertake their training on quarterly and yearly basis respectively. On the other hand, 50 percent of the hotels do training on weekly, monthly and a yearly basis respectively.
IMPLICATIONS
What implications might arise from the study findings and conclusions? First, with regard to the distribution of educational qualification of respondents star rating hotels indicated a more male dominated employee with degree and above working in 4 to 5 star hotels. The implications of this is that a more educated workforce is more adaptive to dynamic security intervention measures required than a less educated workers. Furthermore, the security parameters are evolving and challenging to the hotel operators. This therefore requires informed minds on security procedures and standards to mitigate any security lapse in the hotel industry.
The hotel ownership in Kenya is skewed towards chain affiliated hotels that the majority is foreign investment. Therefore there is likelihood that economic leakage of revenue is being siphoned out of the country. Despite the government creating investment incentives such as generous duty remissions on imported inputs the local communities are not directly benefitting from these hotels a part from employment opportunities provided to low cadre positions.
The implications of the finding based on the results in Table 7 the first extracted component accounted for 49.224 per cent of the total explained variance in the accountants‟ concern regarding the safety and security issues are that hotel management has a great concern in security measures applied in the hotel industry. These are internal control aspects within the kitchen and the store operations, which affects hotel’s profitability.
The internal security measures especially the movements of foodstuffs from one store to another if not effective done will interfere with the gross profit of the hotel industry. Therefore stringent measures are required to curb any such loopholes.
On the cost of security the hotels in a 3 star category in Nairobi spend more by 56 percent than the Coastal hotels in the same category. The cost of security operations in hotels in Nairobi is generally higher than the cost of security investment in Mombasa County.
The market for biometrics in the hotel industry especially in the Kenyan hotels was in the infant stages with only a few of hotels adopting partially the biometric technology so far. Many hotels are reluctant to embrace biometric technology.
The majority of the hotel managers interviewed concurred that the increase of security costs in the hotel industry has led hotels to increase their rates to recover from cost of security investment. This view is consistent with another study by Power and Barrowe (2006).
LIMITATIONS AND FUTURE RESEARCH
This study limitation provides good avenues for further research. First the security parameters are evolving and challenging to the hotel operators. This therefore requires informed minds on security procedures and standards to mitigate any security lapse in the hotel industry. The cadre of the security personnel recruited is of low qualifications whereby they are not effectively able to come up with a pro-active strategy to prevent any cases of terrorism by the militants.
The revenue accrued from the hotel business is unlikely to be properly ploughed back into security investment into the hotel industry because of lack of interest by the hotel ownership which is foreign based. The hotel ownership in Kenya is skewed towards chain affiliated hotels that the majority is foreign investment. Therefore there is likelihood that economic leakage of revenue is being siphoned out of the country.
The study focused more on security of guests than their safety; a study therefore needs to be conducted on the safety of guests in the hotel industry.
The study established that there is no unified security platform where all the stakeholders’ come together to obtain, filter, censure and disseminate any security information which is perceived to have a negative image and destructive to the hotel industry. The recommendations from this study may be perceived differently due to fragmentation and nature of the hotel properties which is not properly controlled and regulated.
The research noted that biometrics applications in the hotel industry in the Kenyan hotels were in the infant stages with only a few of hotels adopting partially the biometric technology so far. Many hotels are reluctant to embrace biometric technology. The government needs to cushion in security devices not only of high quality but also ensure that their functionality is realized.
Benson, P. (2011). Identification Systems: the Importance of Guest Identification Technology. Retrieved from http://www.hotel industry.co.uk/2011/07/identification-systems/.
Chon, K. ., & Sparrowe, R. (1995). Welcome to Hospitality An Introduction. South Western Publishing Company.
Cobanoglu, C., Corbaci, K., Moreo, P.J. & Ekinci, Y. (2003). A Comparative Study of the Importance of Hotel Selection Components by Turkish Business Travelers. International Journal of Hospitality and Tourism Administration, 4, 1-22.
Frey, B. S., Luechinger, S., & Stutze, A. (2007). Calculating Tragedy Assessing the Costs of Terrorism. Blackwell Publishing Ltd.
Henderson, J., Shufen, C., Huifen, L., & Xiang, L. (2005). Tourism and terrorism: The hotel industry perspective in Singapore. Retrieved from http://www.jthca.org
Ikiara, M.M. (2001), Vision and Long Term Development Strategy for Kenyas Tourism Industry. KIPPRA Discussion Nairobi Kenya Institute for Public Policy Research and Analysis.
Kenya Gazette. (2003). The Hotels and Restaurants classification of Hotels and Restaurants Regulation.
Konstanze, A. (2009). Hotel Benchmark survey. Deloitte.
Kothari. (1999). Research Methodology Methods and Techniques.New York USA.
Mansfeld, Y., & Pizam, P. (2006). Tourism security & safety from theory to practice.Burlington MA Elsevier Butterworth Heinemann.
Mugenda, O., & Mugenda, A. (2003). Research methods. Quantitative and Qualitative Approaches. Nairobi Act Press.
Pizam, A. (1999). A comprehensive approach to classifying acts of crime and violence at tourism destination. Journal of Travel Research, 38, 5-12.
Power, I., & Barrows, C. (2006). Introduction to Management in Hospitality Industry Hoboken NY John Wiley & Sons.
Punpugdee, N. (2012). Investigating the process of valuing investments in intangibles A case study in safety and security in the multinational The hotel industry. USA Virginia Polytechnic Institute and State University.
Starmer Smith, C. (2003). 10 cities to beware.
Yoel, M., & Pizam, A. (2006). Tourism Security & Safety from theory to practice.United Kingdom Elsevier Butterw.










